一、说明
利用certbot工具配置Let’s encrypt通配符证书,所域名下所有的子域名都能方便的使用 https证书,而且完全免费。值得关注的是,
Let’s encrypt通配符证书只是针对二级域名,并不能针对主域名,如*.zhl123.com和zhl123.com 被认为是两个域名,
如果和我一样使用的是主域名,在申请的时候需要注意都要申请。
二、环境
操作系统:CentOS Linux release 7.5.1804 (Core)
配置域名:zhl123.com,*.zhl123.com
三、步骤
1. 获取Certbot
# 下载
[root@localhost ~]# wget https://dl.eff.org/certbot-auto
# 设为可执行权限
[root@localhost ~]# chmod u+x certbot-auto
2. 申请证书
[root@localhost ~]# ./certbot-auto certonly -d "*.zhl123.com" -d "zhl123.com" --manual --preferred-challenges dns-01 --server https://acme-v02.api.letsencrypt.org/directory
参数说明:
-certonly,表示安装模式,Certbot 有安装模式和验证模式两种类型的插件。
-manual,表示手动安装插件,Certbot 有很多插件,不同的插件都可以申请证书,用户可以根据需要自行选择。
-d,为哪些主机申请证书,如果是通配符,输入 *.hubinqiang.com(替换为自己的域名)。
-preferred-challenges,使用 DNS 方式校验域名所有权。
-server,Let’s Encrypt ACME v2 版本使用的服务器不同于 v1 版本,需要显示指定。
注意:将zhl123.com替换为自己的域名。可以通过多个-d 参数添加多个主机。
申请过程中需要如下确认:
Creating virtual environment...
Installing Python packages...
Installation succeeded.
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Plugins selected: Authenticator manual, Installer None
Enter email address (used for urgent renewal and security notices) (Enter 'c' to
cancel): 12345@qq.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must
agree in order to register with the ACME server at
https://acme-v02.api.letsencrypt.org/directory
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(A)gree/(C)ancel: A
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Would you be willing to share your email address with the Electronic Frontier
Foundation, a founding partner of the Let's Encrypt project and the non-profit
organization that develops Certbot? We'd like to send you email about our work
encrypting the web, EFF news, campaigns, and ways to support digital freedom.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: Y
Obtaining a new certificate
Performing the following challenges:
dns-01 challenge for zhl123.com
dns-01 challenge for zhl123.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
NOTE: The IP of this machine will be publicly logged as having requested this
certificate. If you're running certbot in manual mode on a machine that is not
your server, please ensure you're okay with that.
Are you OK with your IP being logged?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: Y
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
在域名 DNS 解析中添加 TXT记录:
Please deploy a DNS TXT record under the name
_acme-challenge.zhl123.com with the following value:
hwiixYGDrbozBBmveWtsiI5pJTu5CZJVk3WiYR26DgE
Before continuing, verify the record is deployed.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Press Enter to Continue
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please deploy a DNS TXT record under the name
_acme-challenge.zhl123.com with the following value:
zvW8FMXw81O4t_Drx6tQ1xENk897dg5zHeirZP0a4GI
Before continuing, verify the record is deployed.
(This must be set up in addition to the previous challenges; do not remove,
replace, or undo the previous challenge tasks yet. Note that you might be
asked to create multiple distinct TXT records with the same name. This is
permitted by DNS standards.)
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Press Enter to Continue
Waiting for verification...
Cleaning up challenges
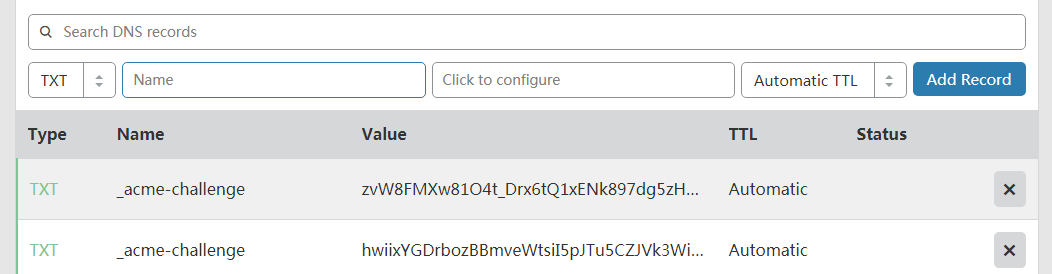
注意:若申请了多个主机,需要添加多个 TXT 记录。要求给 _acme-challenge.zhl123.com 配置 TXT 记录,在没有确认 TXT 记录生效之前不要回车执行。
确认生效后会有如下提示:
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/zhl123.com/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/zhl123.com/privkey.pem
Your cert will expire on 2019-02-13. To obtain a new or tweaked
version of this certificate in the future, simply run certbot-auto
again. To non-interactively renew *all* of your certificates, run
"certbot-auto renew"
- Your account credentials have been saved in your Certbot
configuration directory at /etc/letsencrypt. You should make a
secure backup of this folder now. This configuration directory will
also contain certificates and private keys obtained by Certbot so
making regular backups of this folder is ideal.
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
3. 配置证书
在 nginx 中配置的片段:
server {
server_name zhl123.com;
listen 443 http2 ssl;
ssl on;
ssl_certificate /etc/letsencrypt/live/zhl123.com/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/zhl123.com/privkey.pem;
ssl_trusted_certificate /etc/letsencrypt/live/zhl123.com/chain.pem;
重启 nginx 查看效果。
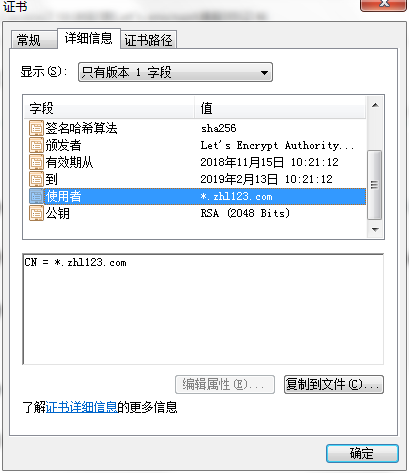
4. 证书更新
Let’s encrypt 的免费证书默认有效期为 90 天,到期后如果要续期可以执行:
$ ./certbot-auto certonly -d *.example.com -d *.example.org -d www.example.cn --manual --preferred-challenges dns --dry-run --manual-auth-hook /脚本目录/au.sh详情请参考:https://github.com/ywdblog/certbot-letencrypt-wildcardcertificates-alydns-au
